As many statistics show, Windows servers steady grows in the world wide market and companies are increasingly building their websites based on Windows infrastructure. Windows operation systems, accompanied with IIS and SQL Server, can be utilized to easily build online game servers, HTTP servers, FTP servers, Email servers, etc. On the other hand, many security issues arises and RDP brute force attack becomes one of the most serious thread. This article shows how to use Anti DDoS Guardian to stop RDP brute force attacks.
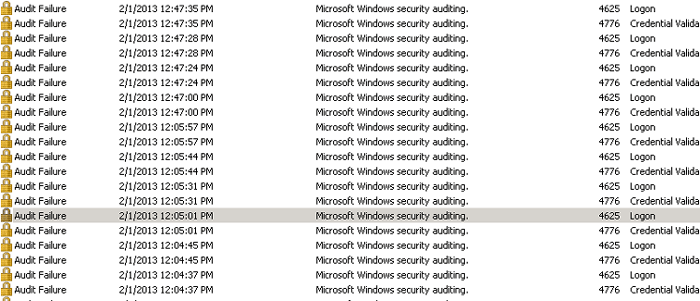
When someone wants to access his Windows server remotely, he probably use Remote Desktop Connection to log on the server. But, what if a bad guy tries random passwords and usernames to log on the server by a smart program? It is easy to find such a program by Google. The worst thing is that many Windows servers have already been hacked without being noticed. If you want to know if your servers are under RDP brute force attacks, please follow the steps bellow to check the audit information(Computer Management>System Tools>Event Viewer>Windows Logs>Security). If you find there are many audit auditing information, say 20 logs per minute, your server must be under such attack.
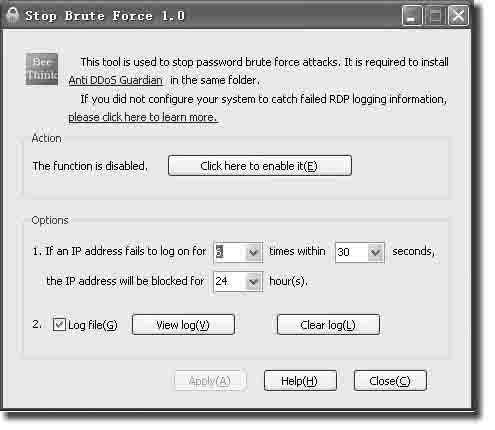
The idea to stop RDP brute force attacks is simple. Anti DDoS Guardian just reads the Windows system RDP failed logging information in Real-Time and puts the bad IP addresses into Anti DDoS Guardian blocking list. If an IP address logs on and fails for several time in a certain period, such as 6 times within 30 seconds, the IP address will be blocked.